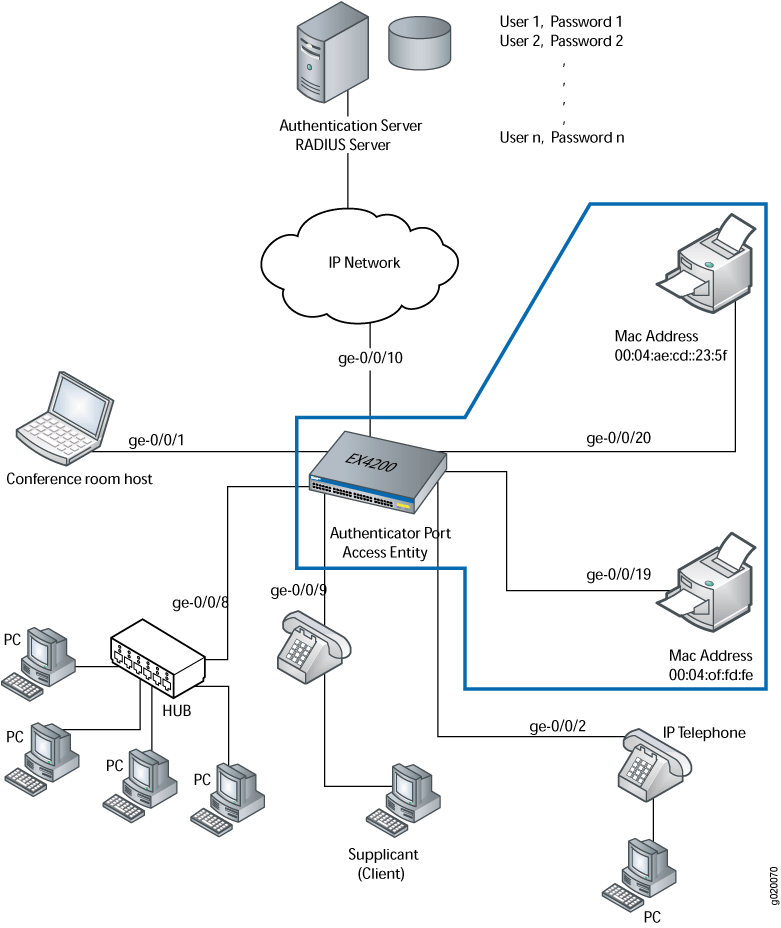
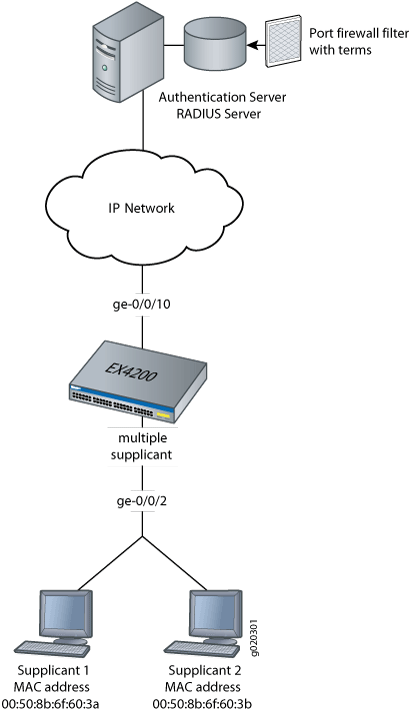
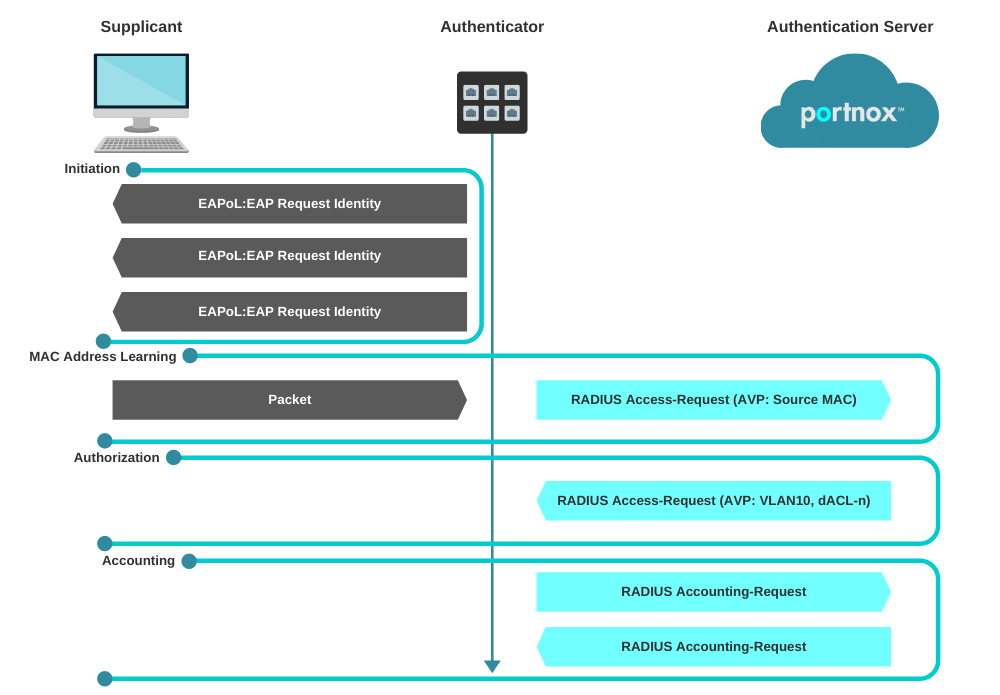
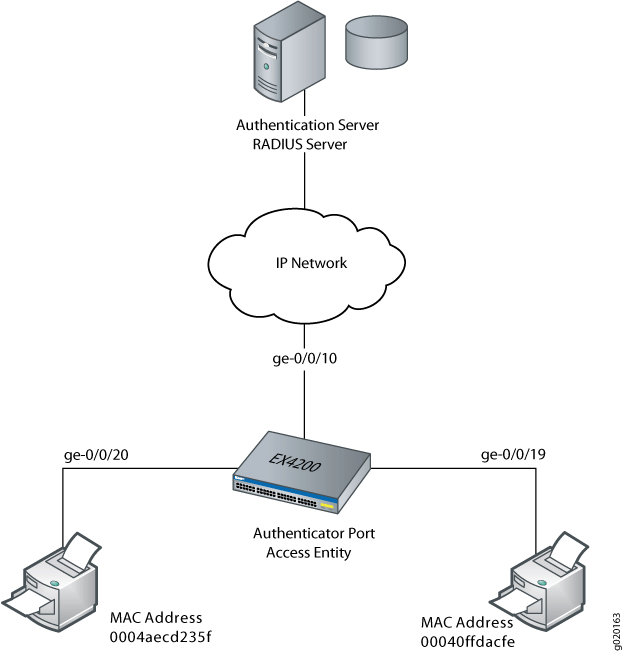
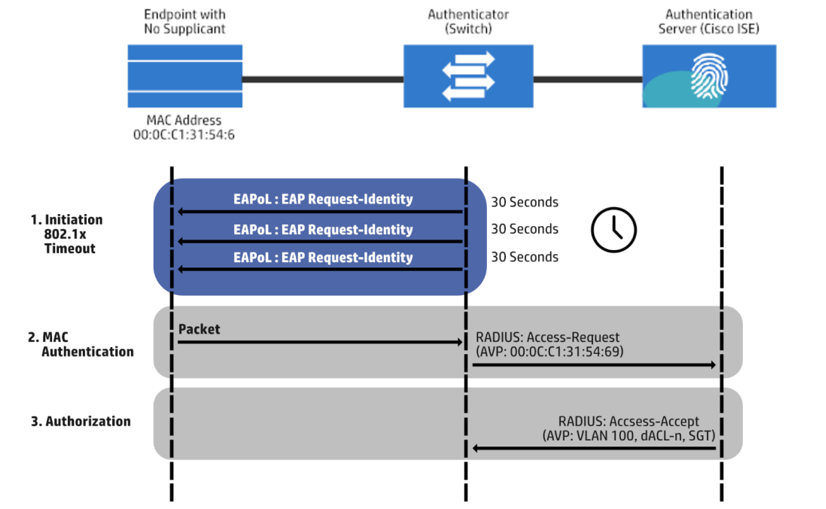
Example for Configuring MAC Address Authentication (AAA RADIUS Authentication Is Used) - S1720, S2700, S5700, and S6720 V200R011C10 Configuration Guide - User Access and Authentication - Huawei
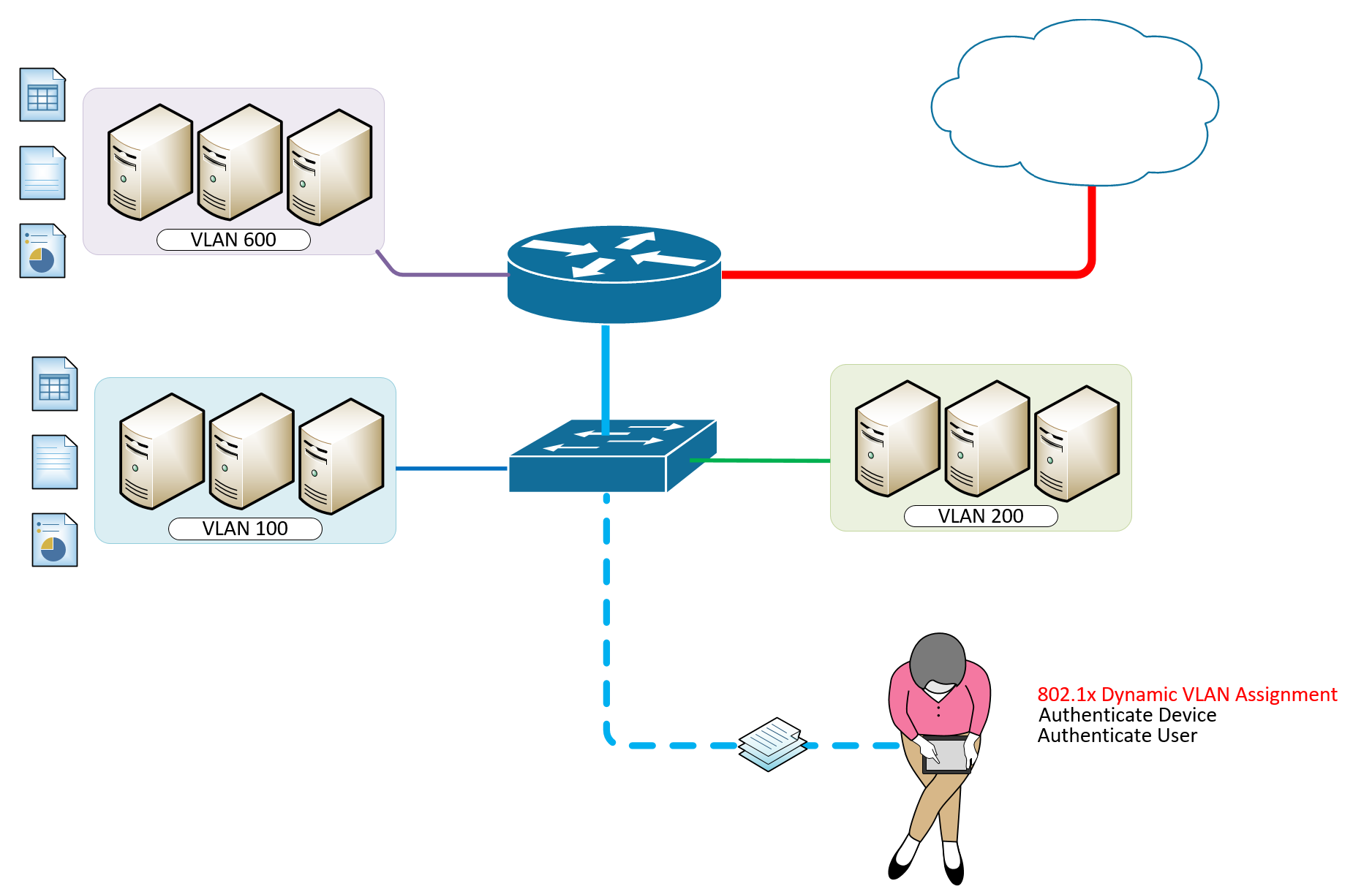
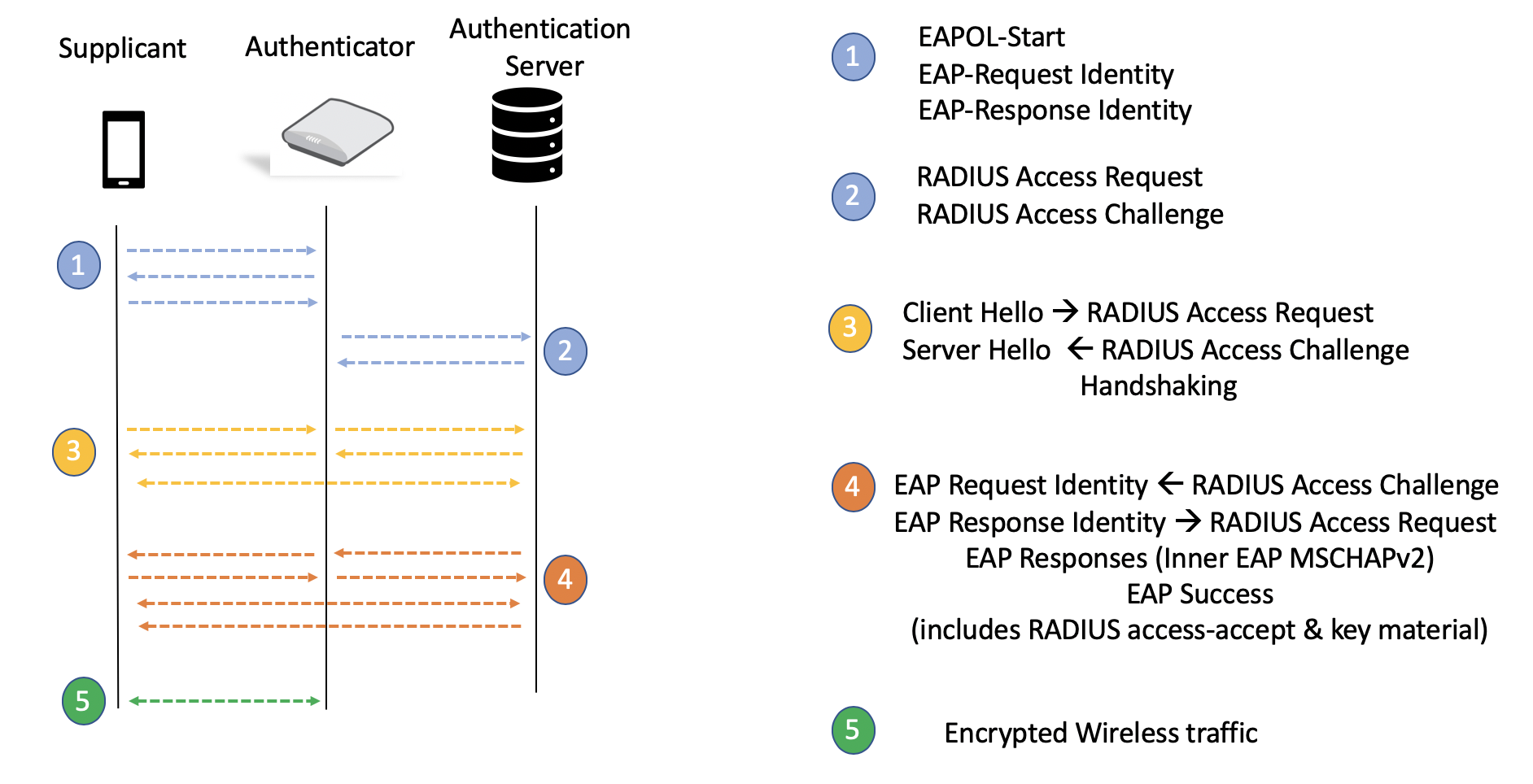
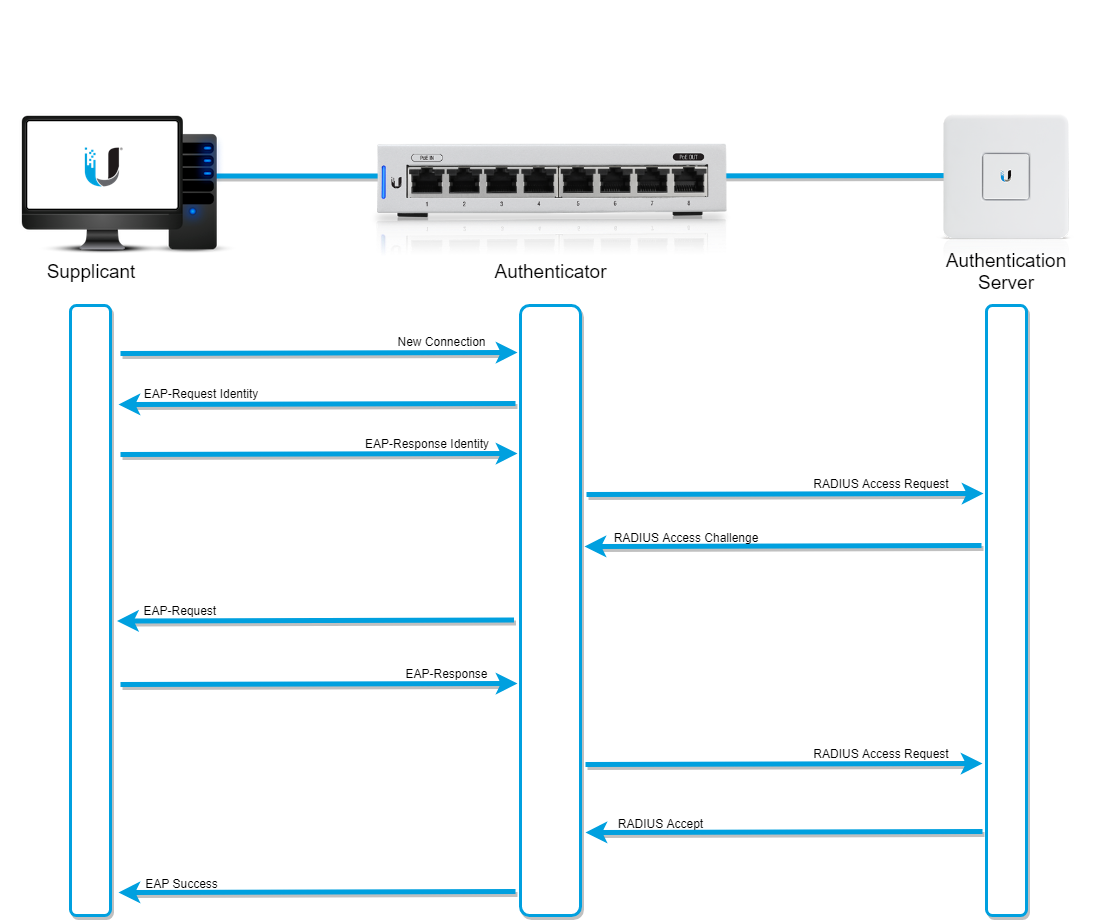
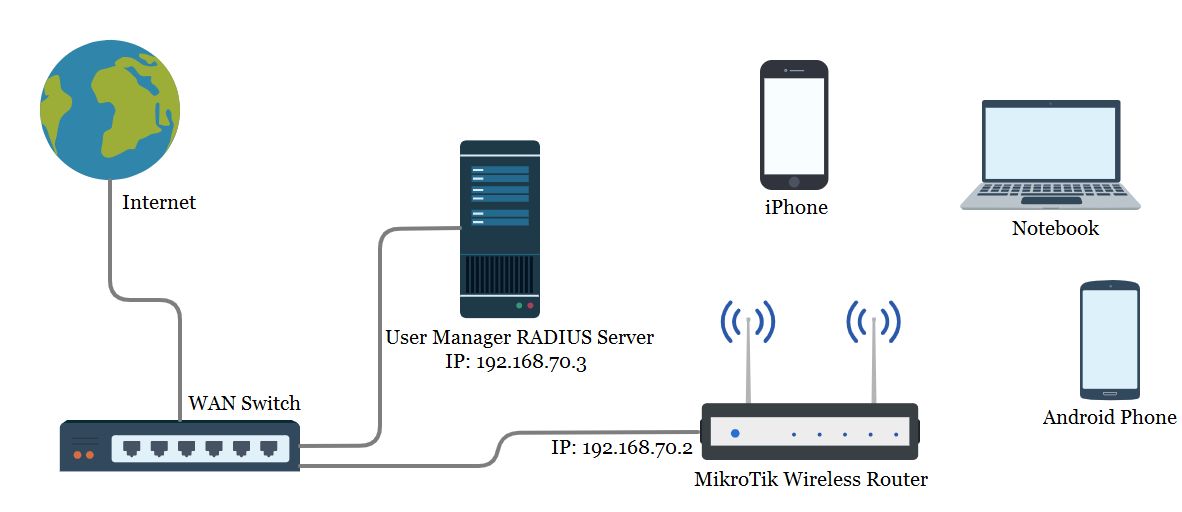
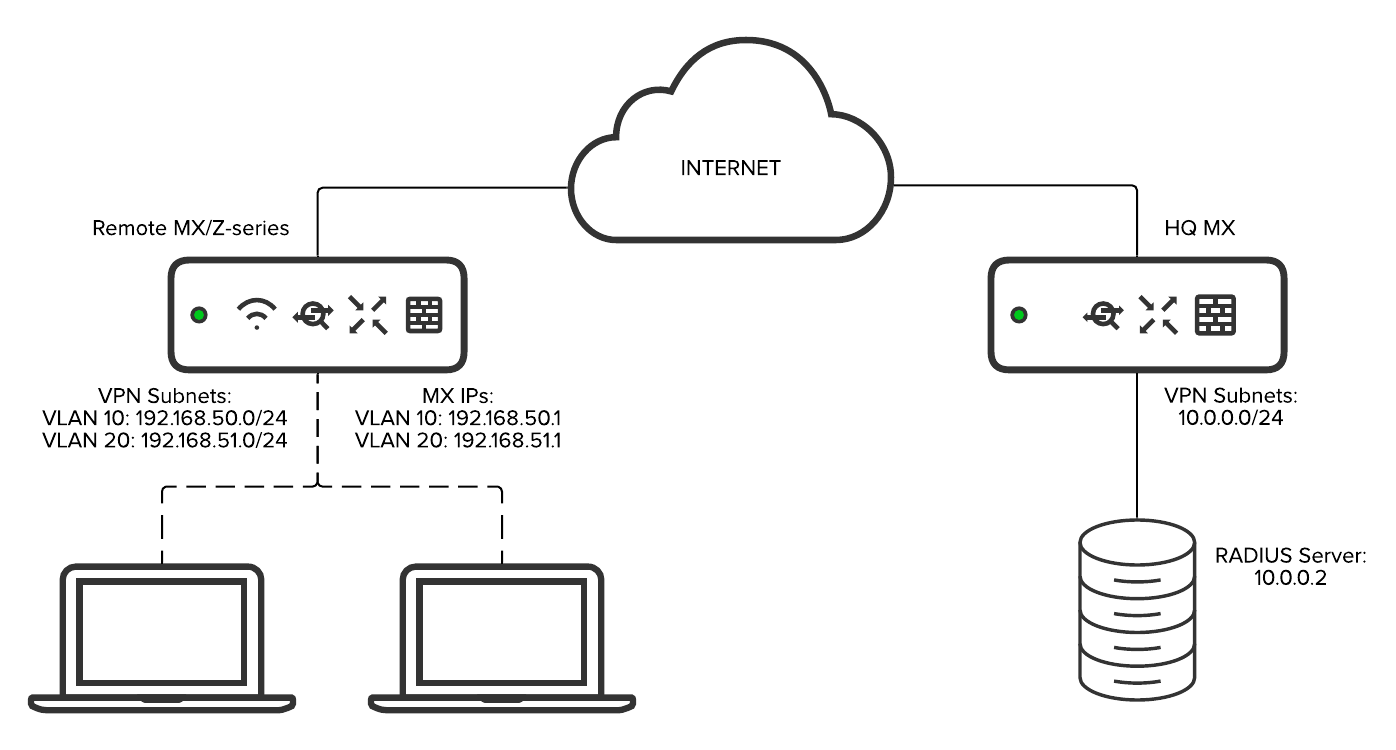
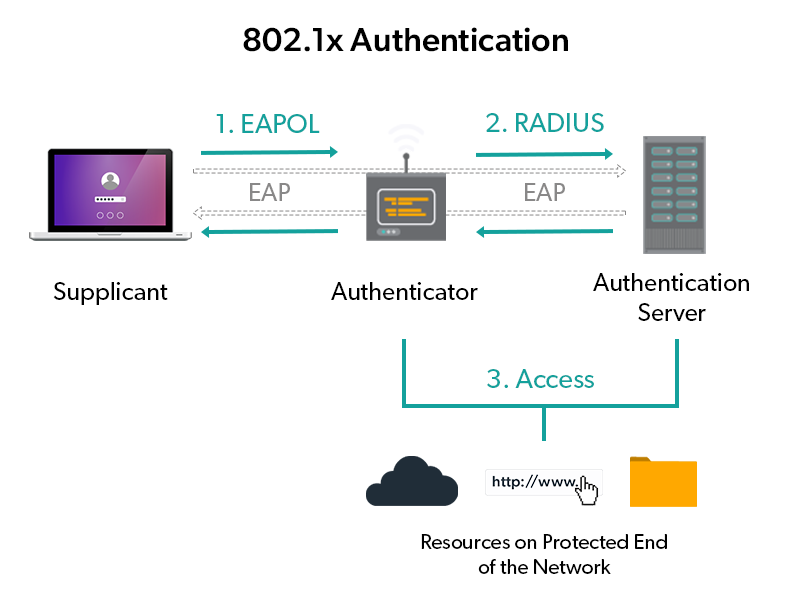
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server - Expert Network Consultant
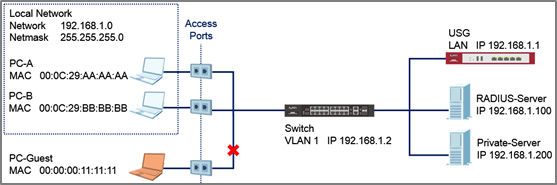
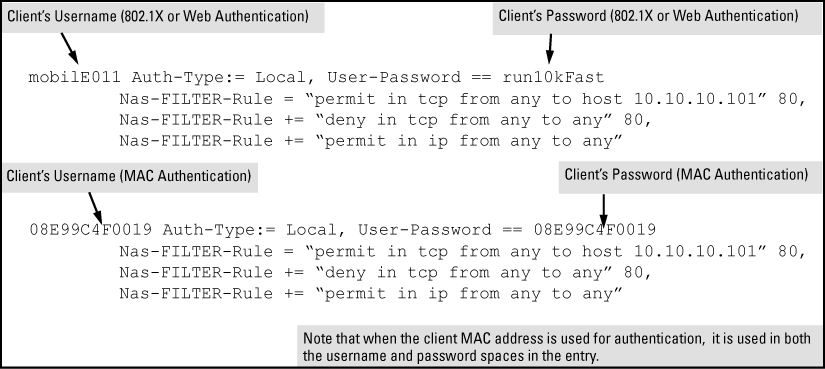
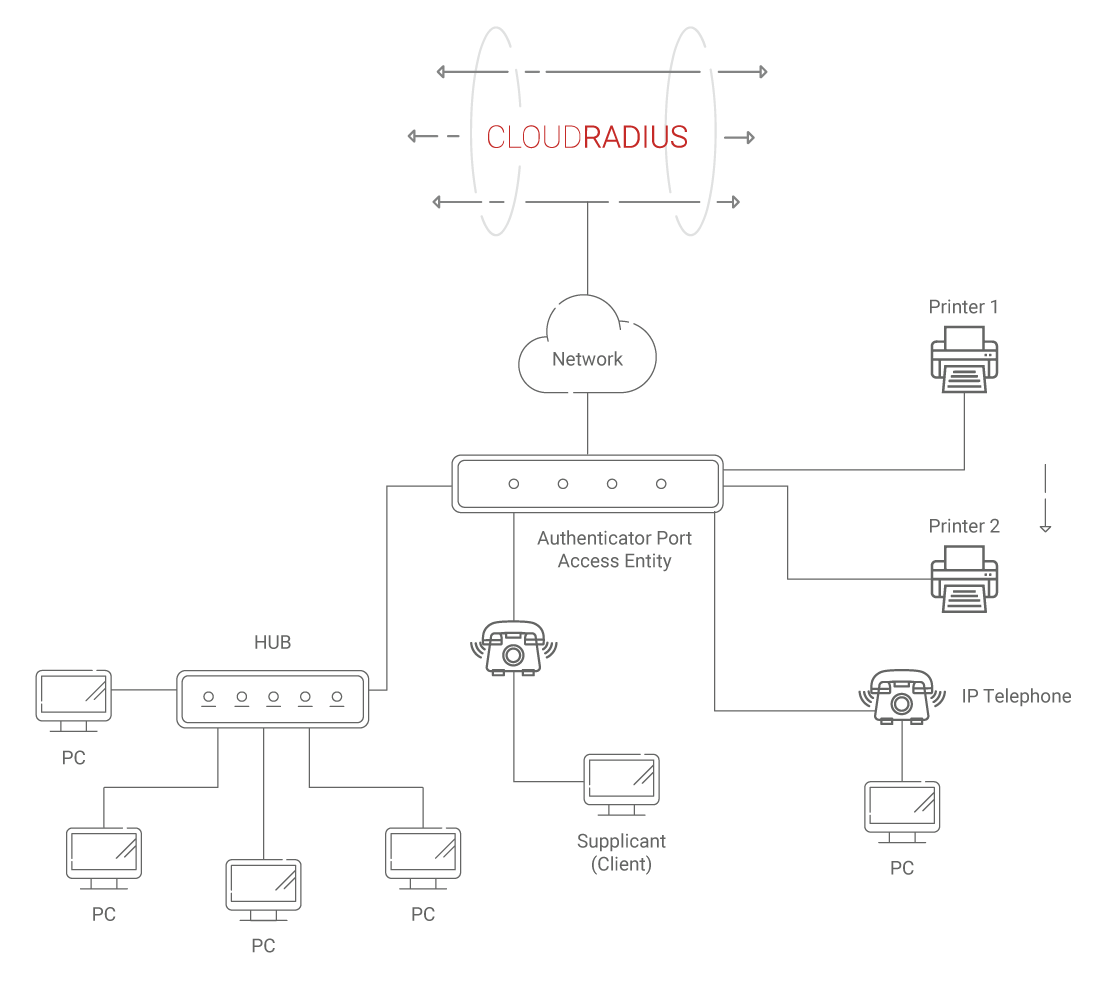
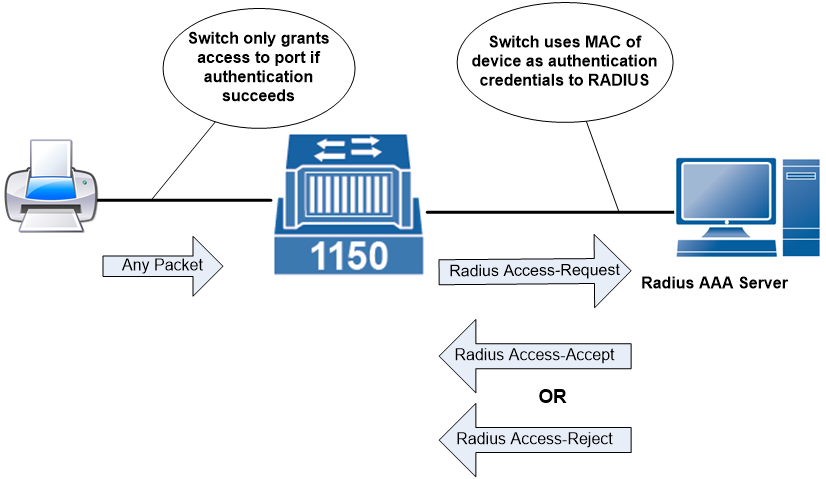
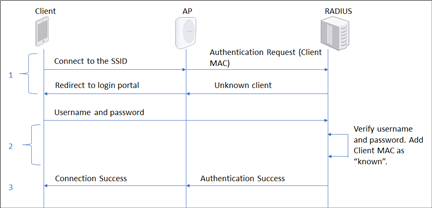
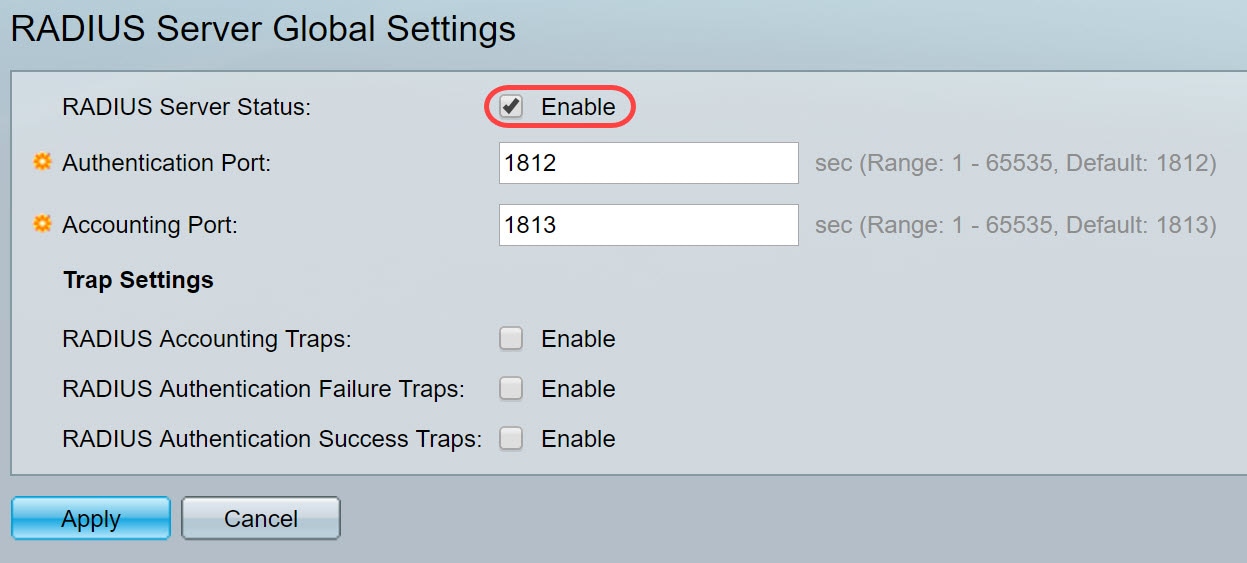
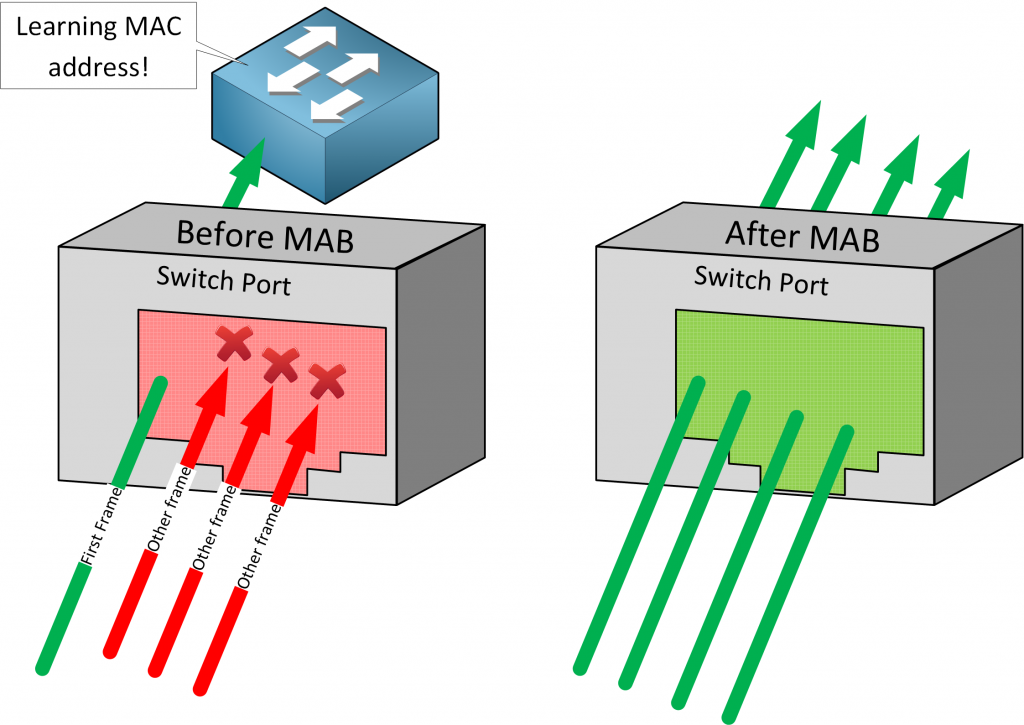
How to configure the switch and RADIUS server to provide network access through device's MAC address — Zyxel Community